大家好,欢迎来到IT知识分享网。
Java实现非对称加密
1. 简介
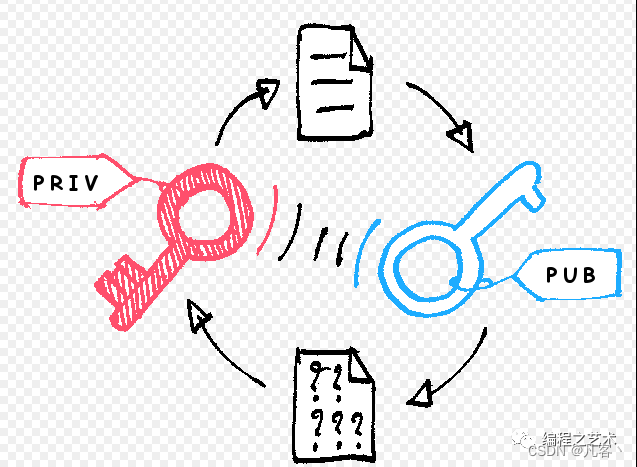
此流程图显示非对称加密过程是单向的,其中一条密钥加密后只能用相对应的另一条密钥解密。
2. 非对称加密算法–DH(密钥交换)
| 密钥长度 | 默认 | 工作模式 | 填充方式 | 实现方 |
|---|---|---|---|---|
| 512~1024(64倍数) | 1024 | 无 | 无 | JDK |
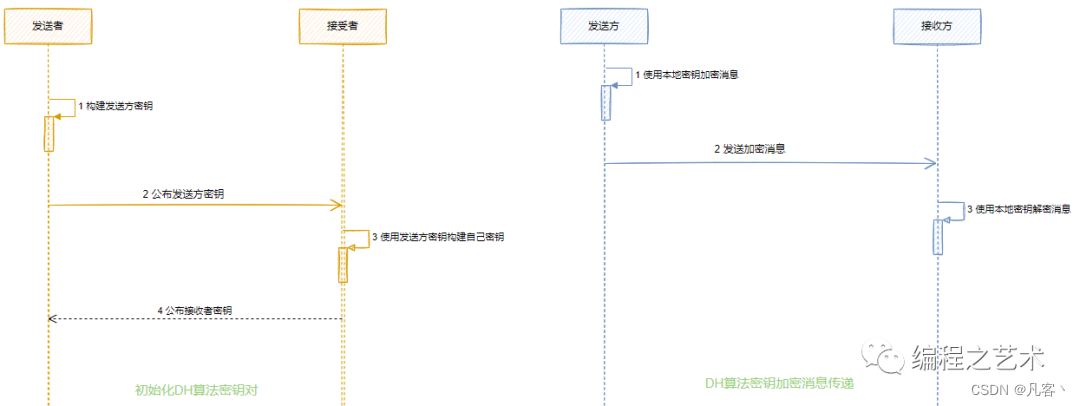
DH加解密应用:
package com.bity.dh; import org.apache.commons.codec.binary.Base64; import javax.crypto.BadPaddingException; import javax.crypto.Cipher; import javax.crypto.IllegalBlockSizeException; import javax.crypto.KeyAgreement; import javax.crypto.NoSuchPaddingException; import javax.crypto.SecretKey; import javax.crypto.interfaces.DHPublicKey; import javax.crypto.spec.DHParameterSpec; import java.nio.charset.StandardCharsets; import java.security.InvalidAlgorithmParameterException; import java.security.InvalidKeyException; import java.security.KeyFactory; import java.security.KeyPair; import java.security.KeyPairGenerator; import java.security.NoSuchAlgorithmException; import java.security.PrivateKey; import java.security.PublicKey; import java.security.spec.InvalidKeySpecException; import java.security.spec.X509EncodedKeySpec; import java.util.Objects; import static java.lang.System.*; / * <p>Title: JdkDh</p > * <p>Description: DH非对称算法实现 </p > * <p>Company: http://www.agree.com</p > * <p>Project: security</p > * * @author <a href="mailto:">WEIQI</a> * @version 1.0 * @date 2022-04-27 19:51 */ public class JdkDh {
private static final String SRC = "I'm DH encryption algorithm"; public static void main(String[] args) {
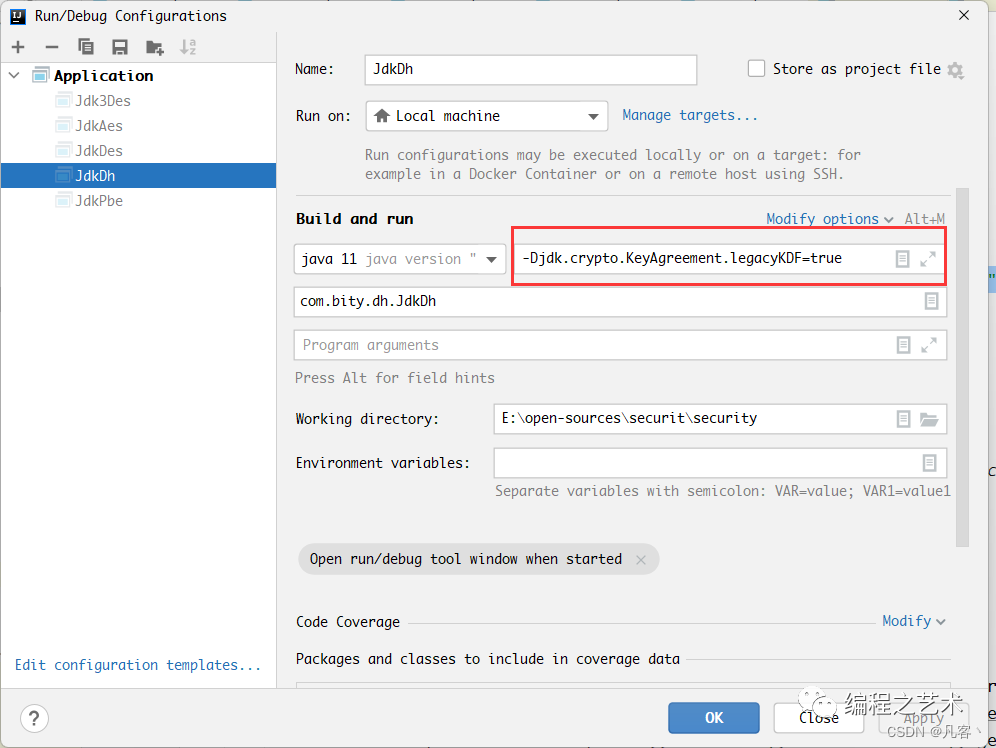
// 解决 Unsupported secret key algorithm: DES 异常 System.getProperties().setProperty("jdk.crypto.KeyAgreement.legacyKDF", "true"); jdkDh(); } private static void jdkDh() {
try {
// 初始化发送方密钥 KeyPairGenerator senderKeyPairGenerator = KeyPairGenerator.getInstance("DH"); senderKeyPairGenerator.initialize(512); KeyPair senderKeyPair = senderKeyPairGenerator.generateKeyPair(); // 发送方密钥,发送给接收方(可以通过文件、优盘、网络等...) byte[] senderPublicKeyEnc = senderKeyPair.getPublic().getEncoded(); // 初始化接收方密钥,注意在实际环境中接收方和发送方肯定不会在一个函数中 KeyFactory keyFactory = KeyFactory.getInstance("DH"); X509EncodedKeySpec x509EncodedKeySpec = new X509EncodedKeySpec(senderPublicKeyEnc); PublicKey receiverPublicKey = keyFactory.generatePublic(x509EncodedKeySpec); DHParameterSpec dhParameterSpec = ((DHPublicKey)receiverPublicKey).getParams(); KeyPairGenerator receiverKeyPairGenerator = KeyPairGenerator.getInstance("DH"); receiverKeyPairGenerator.initialize(dhParameterSpec); KeyPair receiverKeyPair = receiverKeyPairGenerator.generateKeyPair(); PrivateKey receiverPrivateKey = receiverKeyPair.getPrivate(); byte[] receiverPublicKeyEnc = receiverKeyPair.getPublic().getEncoded(); // 构建密钥 KeyAgreement receiverKeyAgreement = KeyAgreement.getInstance("DH"); receiverKeyAgreement.init(receiverPrivateKey); receiverKeyAgreement.doPhase(receiverPublicKey, true); SecretKey receiverSecretKey = receiverKeyAgreement.generateSecret("DES"); KeyFactory senderKeyFactory = KeyFactory.getInstance("DH"); x509EncodedKeySpec = new X509EncodedKeySpec(receiverPublicKeyEnc); PublicKey senderPublicKey = senderKeyFactory.generatePublic(x509EncodedKeySpec); KeyAgreement senderKeyAgreement = KeyAgreement.getInstance("DH"); senderKeyAgreement.init(senderKeyPair.getPrivate()); senderKeyAgreement.doPhase(senderPublicKey, true); SecretKey senderSecretKey = senderKeyAgreement.generateSecret("DES"); if (Objects.equals(receiverSecretKey, senderSecretKey)) {
out.println("双方密钥相同"); } // 加密 Cipher cipher = Cipher.getInstance("DES"); cipher.init(Cipher.ENCRYPT_MODE, senderSecretKey); byte[] result = cipher.doFinal(SRC.getBytes(StandardCharsets.UTF_8)); out.println("jdk dh encryption is : " + Base64.encodeBase64String(result)); // 解密 cipher.init(Cipher.DECRYPT_MODE, receiverSecretKey); result = cipher.doFinal(result); out.println("jdk dh decrypt is : " + new String(result)); } catch (NoSuchAlgorithmException | InvalidKeySpecException | InvalidAlgorithmParameterException | InvalidKeyException | NoSuchPaddingException | IllegalBlockSizeException | BadPaddingException e) {
e.printStackTrace(); } } } 运行结果:
双方密钥相同 jdk dh encryption is : Be3LeXqV/q1PDEbpH62LL129gaV5Og0Eo3GY9e00B4o= jdk dh decrypt is : I'm DH encryption algorithm 注意:由于JDK8 update 161之后,DH的密钥长度至少为512位,但DES算法密钥不能达到这样的长度,所以运行会抛出Unsupported secret key algorithm: DES异常。解决办法有两种如下:
- 在代码中加如下代码:
System.getProperties().setProperty("jdk.crypto.KeyAgreement.legacyKDF", "true"); - 在启动的时候添加JVM变量:-Djdk.crypto.KeyAgreement.legacyKDF=true
3. 非对称加密算法–RSA
RSA加密算法是一种非对称加密算法,在公开密钥加密和电子商业中被广泛使用。RSA是由罗纳德·李维斯特(Ron Rivest)、阿迪·萨莫尔(Adi Shamir)和伦纳德·阿德曼(Leonard Adleman)在1977年一起提出的。当时他们三人都在麻省理工学院工作。RSA 就是他们三人姓氏开头字母拼在一起组成的。
对极大整数做因数分解的难度决定了 RSA 算法的可靠性。换言之,对一极大整数做因数分解愈困难,RSA 算法愈可靠。假如有人找到一种快速因数分解的算法的话,那么用 RSA 加密的信息的可靠性就会极度下降。但找到这样的算法的可能性是非常小的。今天只有短的 RSA 钥匙才可能被强力方式激活成功教程。到2020年为止,世界上还没有任何可靠的攻击RSA算法的方式。只要其钥匙的长度足够长,用RSA加密的信息实际上是不能被激活成功教程的。
RSA算法加密实现:
package com.bity.rsa; import org.apache.commons.codec.binary.Base64; import javax.crypto.BadPaddingException; import javax.crypto.Cipher; import javax.crypto.IllegalBlockSizeException; import javax.crypto.NoSuchPaddingException; import java.nio.charset.StandardCharsets; import java.security.InvalidKeyException; import java.security.KeyFactory; import java.security.KeyPair; import java.security.KeyPairGenerator; import java.security.NoSuchAlgorithmException; import java.security.PrivateKey; import java.security.PublicKey; import java.security.interfaces.RSAPrivateKey; import java.security.interfaces.RSAPublicKey; import java.security.spec.InvalidKeySpecException; import java.security.spec.PKCS8EncodedKeySpec; import java.security.spec.X509EncodedKeySpec; import static java.lang.System.*; / * <p>Title: JdkRsa</p > * <p>Description: RSA非对称加密算法实现 </p > * <p>Company: http://www.agree.com</p > * <p>Project: security</p > * * @author <a href="mailto:">WEIQI</a> * @version 1.0 * @date 2022-04-27 21:38 */ public class JdkRsa {
private static final String SRC = "I'm RSA encryption algorithm"; public static void main(String[] args) {
jdkRsa(); } / * JDK-RSA算法实现 * * @author: <a href="mailto:">WEIQI</a> * @date: 2022-04-28 0:15 */ private static void jdkRsa() {
try {
// 初始化密钥 KeyPairGenerator keyPairGenerator = KeyPairGenerator.getInstance("RSA"); keyPairGenerator.initialize(512); KeyPair keyPair = keyPairGenerator.generateKeyPair(); RSAPublicKey rsaPublicKey = (RSAPublicKey) keyPair.getPublic(); RSAPrivateKey rsaPrivateKey = (RSAPrivateKey) keyPair.getPrivate(); out.println("public key is : " + Base64.encodeBase64String(rsaPublicKey.getEncoded())); out.println("private key is : " + Base64.encodeBase64String(rsaPrivateKey.getEncoded())); // 私钥加密,公钥解密 -- 加密 PKCS8EncodedKeySpec pkcs8EncodedKeySpec = new PKCS8EncodedKeySpec(rsaPrivateKey.getEncoded()); KeyFactory keyFactory = KeyFactory.getInstance("RSA"); PrivateKey privateKey = keyFactory.generatePrivate(pkcs8EncodedKeySpec); Cipher cipher = Cipher.getInstance("RSA"); cipher.init(Cipher.ENCRYPT_MODE, privateKey); byte[] result = cipher.doFinal(SRC.getBytes(StandardCharsets.UTF_8)); out.println("私钥加密,公钥解密 -- 加密 : " + Base64.encodeBase64String(result)); // 私钥加密,公钥解密 -- 解密 X509EncodedKeySpec x509EncodedKeySpec = new X509EncodedKeySpec(rsaPublicKey.getEncoded()); keyFactory = KeyFactory.getInstance("RSA"); PublicKey publicKey = keyFactory.generatePublic(x509EncodedKeySpec); cipher.init(Cipher.DECRYPT_MODE, publicKey); result = cipher.doFinal(result); out.println("私钥加密,公钥解密 -- 解密 : " + new String(result)); // 公钥加密,私钥解密 -- 加密 cipher.init(Cipher.ENCRYPT_MODE, publicKey); byte[] res = cipher.doFinal(SRC.getBytes(StandardCharsets.UTF_8)); out.println("公钥加密,私钥解密 -- 加密 : " + Base64.encodeBase64String(res)); // 公钥加密,私钥解密 -- 解密 cipher.init(Cipher.DECRYPT_MODE, privateKey); res = cipher.doFinal(res); out.println("公钥加密,私钥解密 -- 解密 : " + new String(res)); } catch (NoSuchAlgorithmException | InvalidKeySpecException | NoSuchPaddingException | InvalidKeyException | IllegalBlockSizeException | BadPaddingException e) {
e.printStackTrace(); } } } 运行结果:
public key is : MFwwDQYJKoZIhvcNAQEBBQADSwAwSAJBAIfDTXqCrjGHP9tCmLujavsngP8nqSHIl/JkFN8ZmQEcn48xzSXdijEG8Ssgm3SkDWICT0cW9wf3mZ+UkVxLx90CAwEAAQ== private key is : MIIBVQIBADANBgkqhkiG9w0BAQEFAASCAT8wggE7AgEAAkEAh8NNeoKuMYc/20KYu6Nq+yeA/yepIciX8mQU3xmZARyfjzHNJd2KMQbxKyCbdKQNYgJPRxb3B/eZn5SRXEvH3QIDAQABAkASyfa5E8jj1eICiE72+QDfTXJO3cBMiqRsyWkSD0rbmlL/Qv1xDDQonWM58sIR6DOBWQZ+uXbkL1VtOuZ9sgfBAiEA9IxhRwkTYA1GVUKmgZPX+7CsfUmIZi8P/r9/C29XQZUCIQCOHtBkIOupaTLPv3A4yznEidygfbL8nrLV2Xhf6wVrKQIhAJ+RdewPDPhw0QLTIaiNWrIdXv/FWl4quUolk/VXKl1dAiASpbpkGOmy7cmr9otr+EZZIlmfeT695LjEVGd19mlcmQIhAJfua+j3/PT0+z0nPIaGDvczviyl5SxmDo79rfMNpi10 私钥加密,公钥解密 -- 加密 : AiYjJSlGlz5x86mwVW/wjieG/uJsoLEqF+xRcPLzq2HL7yIrSrE3oT4wibrvUDR6kp37eHvFaAT+/wVYCreVvg== 私钥加密,公钥解密 -- 解密 : I'm RSA encryption algorithm 公钥加密,私钥解密 -- 加密 : Io2diORtKbeTz5eOOziHrqZKzS1K19U4t3YPydhM4w2LrzW7bJK/d4DQrWTBAhg8rt28OjbGcJfqd1w8MMy4iw== 公钥加密,私钥解密 -- 解密 : I'm RSA encryption algorithm 从上面例子可以看出RSA算法是支持私钥加密、公钥解密和公钥加密、私钥解密的算法。RSA也是唯一被广泛接受并实现的非对称加密算法,从某种程度来说,RSA已经成为非对称加密算法的一个标准了。
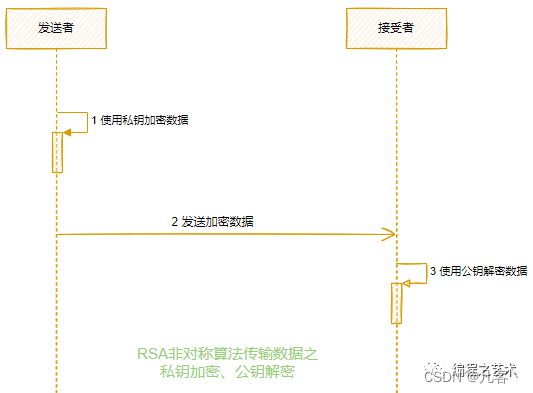
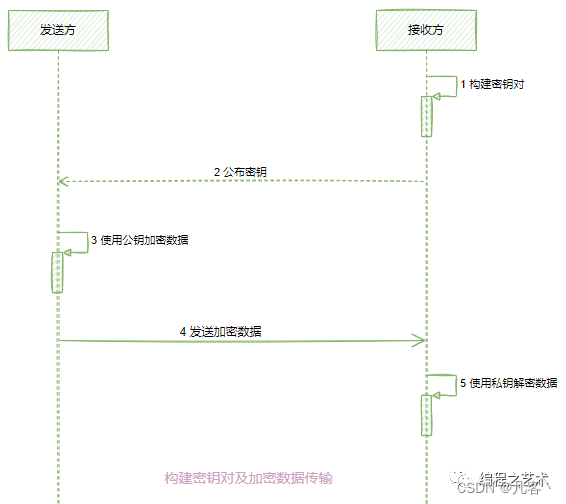
RSA数据加密传输图示:
非对称加密算法–EIGamal
ElGamal算法加解密应用:
package com.bity.eigamal; import org.apache.commons.codec.binary.Base64; import org.bouncycastle.jce.provider.BouncyCastleProvider; import javax.crypto.BadPaddingException; import javax.crypto.Cipher; import javax.crypto.IllegalBlockSizeException; import javax.crypto.NoSuchPaddingException; import javax.crypto.spec.DHParameterSpec; import java.nio.charset.StandardCharsets; import java.security.AlgorithmParameterGenerator; import java.security.AlgorithmParameters; import java.security.InvalidAlgorithmParameterException; import java.security.InvalidKeyException; import java.security.KeyFactory; import java.security.KeyPair; import java.security.KeyPairGenerator; import java.security.NoSuchAlgorithmException; import java.security.PrivateKey; import java.security.PublicKey; import java.security.SecureRandom; import java.security.Security; import java.security.spec.InvalidKeySpecException; import java.security.spec.InvalidParameterSpecException; import java.security.spec.PKCS8EncodedKeySpec; import java.security.spec.X509EncodedKeySpec; import static java.lang.System.out; / * <p>Title: BouncyCastleEiGamal</p > * <p>Description: ElGamal加密算法实现 </p > * <p>Company: http://www.agree.com</p > * <p>Project: security</p > * * @author <a href="mailto:">WEIQI</a> * @version 1.0 * @date 2022-04-28 0:38 */ public class BouncyCastleElGamal {
private static final String SRC = "I'm ElGamal encryption algorithm"; public static void main(String[] args) {
bcElGamal(); } private static void bcElGamal() {
try {
Security.addProvider(new BouncyCastleProvider()); AlgorithmParameterGenerator algorithmParameterGenerator = AlgorithmParameterGenerator .getInstance("ElGamal"); algorithmParameterGenerator.init(256); AlgorithmParameters algorithmParameters = algorithmParameterGenerator.generateParameters(); DHParameterSpec dhParameterSpec = algorithmParameters.getParameterSpec(DHParameterSpec.class); // 初始化密钥 KeyPairGenerator keyPairGenerator = KeyPairGenerator.getInstance("ElGamal"); keyPairGenerator.initialize(dhParameterSpec, new SecureRandom()); KeyPair keyPair = keyPairGenerator.generateKeyPair(); PublicKey elGamalPublicKey = keyPair.getPublic(); PrivateKey elGamalPrivateKey = keyPair.getPrivate(); out.println("public key is : " + Base64.encodeBase64String(elGamalPublicKey.getEncoded())); out.println("private key is : " + Base64.encodeBase64String(elGamalPrivateKey.getEncoded())); // 公钥加密,私钥解密 -- 加密 X509EncodedKeySpec x509EncodedKeySpec = new X509EncodedKeySpec(elGamalPublicKey.getEncoded()); KeyFactory keyFactory = KeyFactory.getInstance("ElGamal"); PublicKey publicKey = keyFactory.generatePublic(x509EncodedKeySpec); Cipher cipher = Cipher.getInstance("ElGamal"); cipher.init(Cipher.ENCRYPT_MODE, publicKey); byte[] result = cipher.doFinal(SRC.getBytes(StandardCharsets.UTF_8)); out.println("私钥加密,公钥解密 -- 解密 : " + Base64.encodeBase64String(result)); // 公钥加密,私钥解密 -- 解密 PKCS8EncodedKeySpec pkcs8EncodedKeySpec = new PKCS8EncodedKeySpec(elGamalPrivateKey.getEncoded()); keyFactory = KeyFactory.getInstance("ElGamal"); PrivateKey privateKey = keyFactory.generatePrivate(pkcs8EncodedKeySpec); cipher.init(Cipher.DECRYPT_MODE, privateKey); result = cipher.doFinal(result); out.println("私钥加密,公钥解密 -- 加密 : " + new String(result)); } catch (NoSuchAlgorithmException | InvalidKeySpecException | NoSuchPaddingException | InvalidKeyException | IllegalBlockSizeException | BadPaddingException | InvalidParameterSpecException | InvalidAlgorithmParameterException e) {
e.printStackTrace(); } } } 运行结果:
public key is : MHYwTwYGKw4HAgEBMEUCIQCxvT1SNSrVl1/8KpvPhaE1MKiaXOHWk5SACDd39SfnHwIgQ5O8oKi9mIKhEDOCKwvYB+mozFgvmuoipw/ZDl6xCicDIwACIBh0K6bn2mtdvmiSMJj/HDlotAGOmTRFMZs+PFoIobQG private key is : MHgCAQAwTwYGKw4HAgEBMEUCIQCxvT1SNSrVl1/8KpvPhaE1MKiaXOHWk5SACDd39SfnHwIgQ5O8oKi9mIKhEDOCKwvYB+mozFgvmuoipw/ZDl6xCicEIgIge9eM9ELM12n6bQKkj8iBtIXjvPeN5mwX9clNriqfSsA= 私钥加密,公钥解密 -- 解密 : e39h4LkKXQn1EIXdDkIxmWiB2pwgO5dZJcNfSmlXqS07SrW1VSLrx0L3RhdWm8hPLaqBZieR5quU/7oTzH/uuA== 私钥加密,公钥解密 -- 加密 : I'm ElGamal encryption algorithm ElGamal数据加密传输图示:
5. 总结
6 案例
6.1 案例1
package com.test; import javax.crypto.Cipher; import java.nio.charset.StandardCharsets; import java.security.*; import java.security.interfaces.RSAPrivateKey; import java.security.interfaces.RSAPublicKey; import java.security.spec.PKCS8EncodedKeySpec; import java.security.spec.X509EncodedKeySpec; import java.util.Base64; public class MyTest02 {
public static void main(String[] args) throws Exception {
MyTest02 myTest02 = new MyTest02(); myTest02.test1(); //生成密钥 String jm = myTest02.test2(); //通过公钥加密 myTest02.test3(jm); //通过私钥解密 } public void test1() throws NoSuchAlgorithmException {
// 初始化密钥 KeyPairGenerator keyPairGenerator = KeyPairGenerator.getInstance("RSA"); keyPairGenerator.initialize(512); KeyPair keyPair = keyPairGenerator.generateKeyPair(); RSAPublicKey rsaPublicKey = (RSAPublicKey) keyPair.getPublic(); RSAPrivateKey rsaPrivateKey = (RSAPrivateKey) keyPair.getPrivate(); System.out.println("public key is : " + Base64.getEncoder().encodeToString(rsaPublicKey.getEncoded())); System.out.println("private key is : " + Base64.getEncoder().encodeToString(rsaPrivateKey.getEncoded())); } public String test2() throws Exception {
String SRC = "I'm RSA encryption algorithm"; String pubKey = "MFwwDQYJKoZIhvcNAQEBBQADSwAwSAJBAIOz/OOCWjqI/6gssHGA/cHiJnR3hNdp230g1x7Y/aWzFc8WrQnjlX4vtdzgDAlz4gMTLkLdU30CAwEAAQ=="; byte[] pubKeyDecode = Base64.getDecoder().decode(pubKey); X509EncodedKeySpec x509EncodedKeySpec = new X509EncodedKeySpec(pubKeyDecode); KeyFactory keyFactory = KeyFactory.getInstance("RSA"); PublicKey publicKey = keyFactory.generatePublic(x509EncodedKeySpec); Cipher cipher = Cipher.getInstance("RSA"); cipher.init(Cipher.ENCRYPT_MODE, publicKey); byte[] res = cipher.doFinal(SRC.getBytes(StandardCharsets.UTF_8)); System.out.println("公钥加密,私钥解密 -- 加密 : " + Base64.getEncoder().encodeToString(res)); return Base64.getEncoder().encodeToString(res); } public void test3 (String data) throws Exception {
String pvtKey = "MIIBVAIBADANBgkqhkiG9w0BAQEFAASCAT4wggE6AgEAAkEAg7P844JaOoj/qCywcYD9weImdHeE12nbfSDXHtj9pbMVzxatCeOVfi/Q90Q6mF+S3wK13OAMCXPiAxMuQt1TfQIDAQABAkAbcnUvjMj1DfwJtlaHMRSxRUoyV34tznfZmfB7E0m5MEwfA="; byte[] pvtDecoder = Base64.getDecoder().decode(pvtKey); PKCS8EncodedKeySpec pkcs8EncodedKeySpec = new PKCS8EncodedKeySpec(pvtDecoder); KeyFactory keyFactory = KeyFactory.getInstance("RSA"); PrivateKey privateKey = keyFactory.generatePrivate(pkcs8EncodedKeySpec); Cipher cipher = Cipher.getInstance("RSA"); cipher.init(Cipher.DECRYPT_MODE, privateKey); byte[] decode = Base64.getDecoder().decode(data); byte[] res = cipher.doFinal(decode); System.out.printf("公钥加密,私钥解密 -- 解密: " + new String(res)); } 6.2 案例2
import java.security.KeyPair; import java.security.KeyPairGenerator; import java.security.PrivateKey; import java.security.PublicKey; import java.util.Base64; import javax.crypto.Cipher; public class RSAEncryptionExample {
public static void main(String[] args) throws Exception {
String data = "Hello, world!"; KeyPair keyPair = KeyPairGenerator.getInstance("RSA").generateKeyPair(); PublicKey publicKey = keyPair.getPublic(); PrivateKey privateKey = keyPair.getPrivate(); Cipher cipher = Cipher.getInstance("RSA"); cipher.init(Cipher.ENCRYPT_MODE, publicKey); byte[] encryptedData = cipher.doFinal(data.getBytes()); System.out.println(Base64.getEncoder().encodeToString(encryptedData)); cipher.init(Cipher.DECRYPT_MODE, privateKey); byte[] decryptedData = cipher.doFinal(encryptedData); System.out.println(new String(decryptedData)); } } 6.3 案例3
import javax.crypto.Cipher; import java.security.KeyPair; import java.security.KeyPairGenerator; import java.security.interfaces.RSAPrivateKey; import java.security.interfaces.RSAPublicKey; / * Description : * * @author : * Date : Created in 20:32 2023/3/13 * @version : */ public class RSATest {
public static void main(String[] args)throws Exception {
//获取RSA算法的密钥生成器对象 KeyPairGenerator keyPairGen =KeyPairGenerator.getInstance("RSA"); //设定密钥长度为1024位 keyPairGen.initialize(1024); //生成"密钥对"对象 KeyPair keyPair = keyPairGen.generateKeyPair(); //分别获取私钥和公钥对象 RSAPrivateKey PrivateKey =(RSAPrivateKey) keyPair.getPrivate(); RSAPublicKey publicKey =(RSAPublicKey) keyPair.getPublic(); //执行加密和解密过程 String InData="Hello World!"; //得到要加密内容的数组 byte[] byteInData =InData.getBytes("UTF-8"); //用公钥加密 byte[] cipherByte= encrypt(publicKey,byteInData); //RSA加密 String cipher=new String(encode(cipherByte)); //Base64a编码 System.out.println("公钥加密,密文:"+cipher); //用私钥解密 byte[] plain =decrypt(PrivateKey,decode(cipher)); //Base64a解码 System.out.println("私钥解密,明文:"+new String(plain)); //RSA解密 } / * 编码 * @param txt byte字节数组 * @return encode Base64编码 */ public static byte[] encode(byte[] txt) {
return org.apache.commons.codec.binary.Base64.encodeBase64(txt); } / * 解码 * @param txt 编码后的byte * @return decode Base64解码 */ public static byte[] decode(String txt){
return org.apache.commons.codec.binary.Base64.decodeBase64(txt); } / * 公钥加密 * @param publicKey 公钥 * @param obj 明文 * @return byte[] 密文 */ public static byte[] encrypt(RSAPublicKey publicKey, byte[] obj) throws Exception {
Cipher cipher =Cipher.getInstance("RSA"); cipher.init(Cipher.ENCRYPT_MODE,publicKey); //返回加密后的内容 return cipher.doFinal(obj); } / * 私钥解密 * @param privateKey 公钥 * @param obj 密文 * @return byte[] 密文 */ public static byte[] decrypt(RSAPrivateKey privateKey, byte[] obj)throws Exception {
Cipher cipher = Cipher.getInstance("RSA"); cipher.init(Cipher.DECRYPT_MODE, privateKey); //返回解密后的数组 return cipher.doFinal(obj); } } 免责声明:本站所有文章内容,图片,视频等均是来源于用户投稿和互联网及文摘转载整编而成,不代表本站观点,不承担相关法律责任。其著作权各归其原作者或其出版社所有。如发现本站有涉嫌抄袭侵权/违法违规的内容,侵犯到您的权益,请在线联系站长,一经查实,本站将立刻删除。 本文来自网络,若有侵权,请联系删除,如若转载,请注明出处:https://haidsoft.com/110403.html