大家好,欢迎来到IT知识分享网。
为了保证客户端和服务器端的可靠连接,TCP建立连接时必须要进行三次会话,也叫TCP三次握手,进行三次握手的目的是为了确认双方的接收能力和发送能力是否正常。
端口扫描
端口扫描的原理
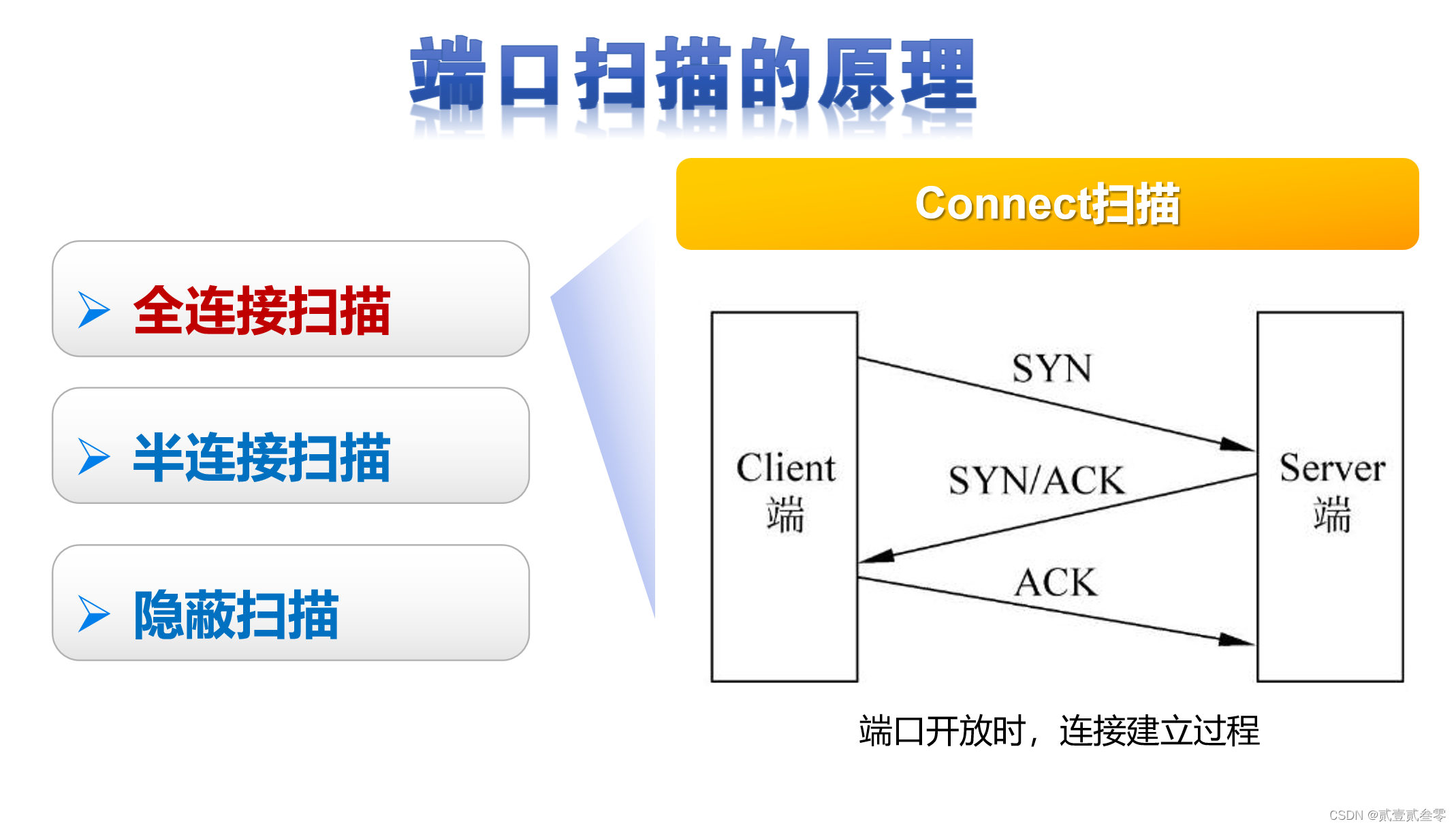
全连接扫描是TCP端口扫描的基础,TCP connect()扫描的实现原理如下所述:
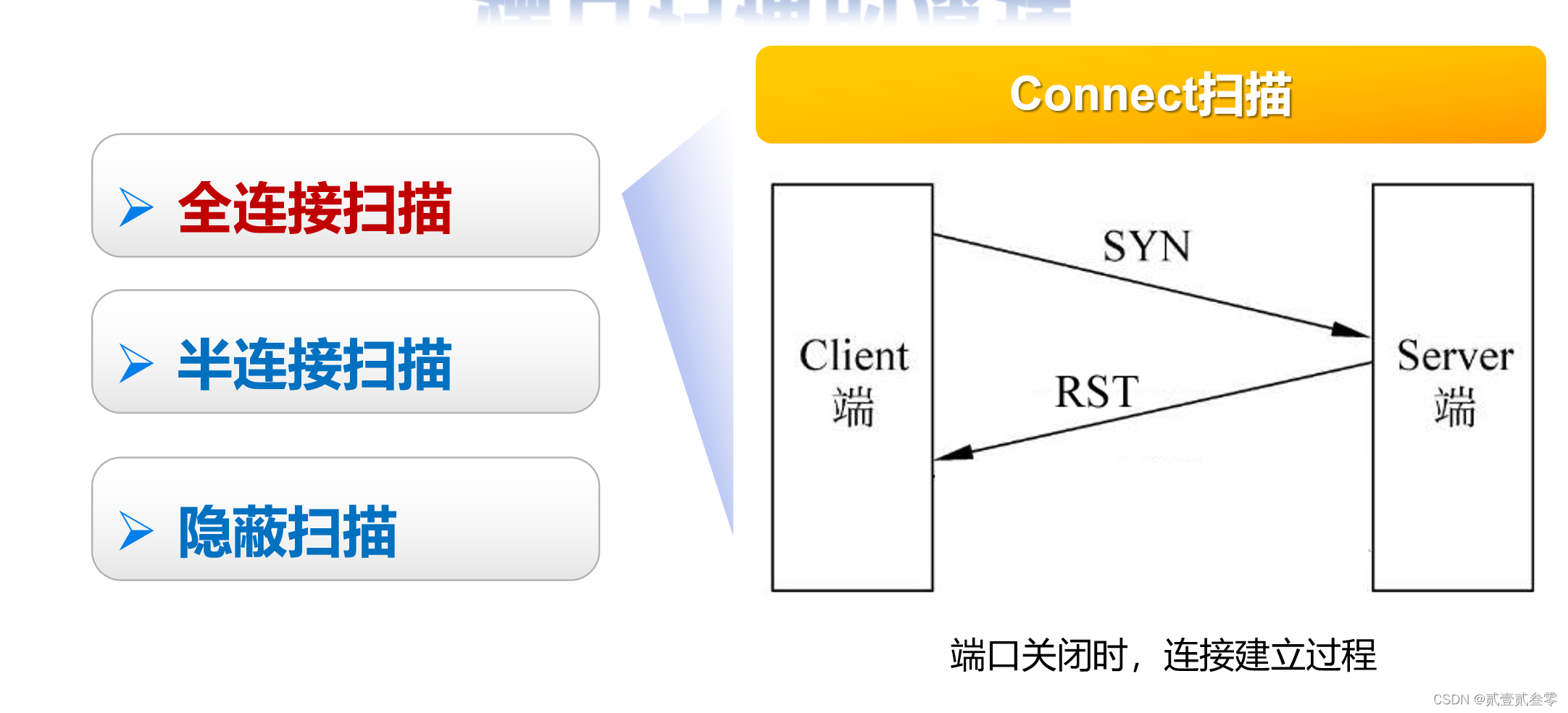
扫描主机通过TCP/IP协议的三次握手与目标主机的指定端口建立一次完整的连接。连接由系统调用connect开始。如果端口开放,则连接将建立成功;否则,若返回-1则表示端口关闭。建立连接成功:响应扫描主机的SYN/ACK连接请求,这一响应表明目标端口处于监听(打开)的状态。如果目标端口处于关闭状态,则目标主机会向扫描主机发送RST的响应。
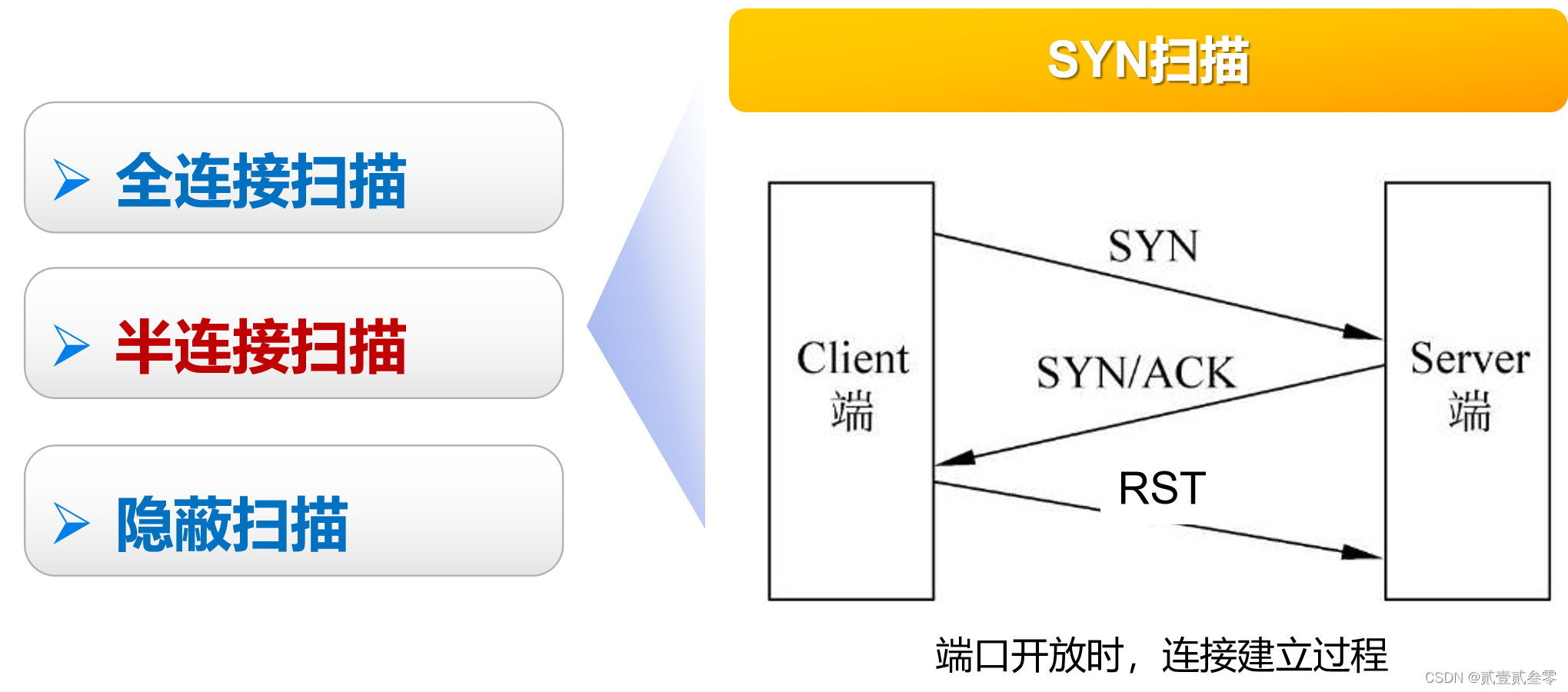
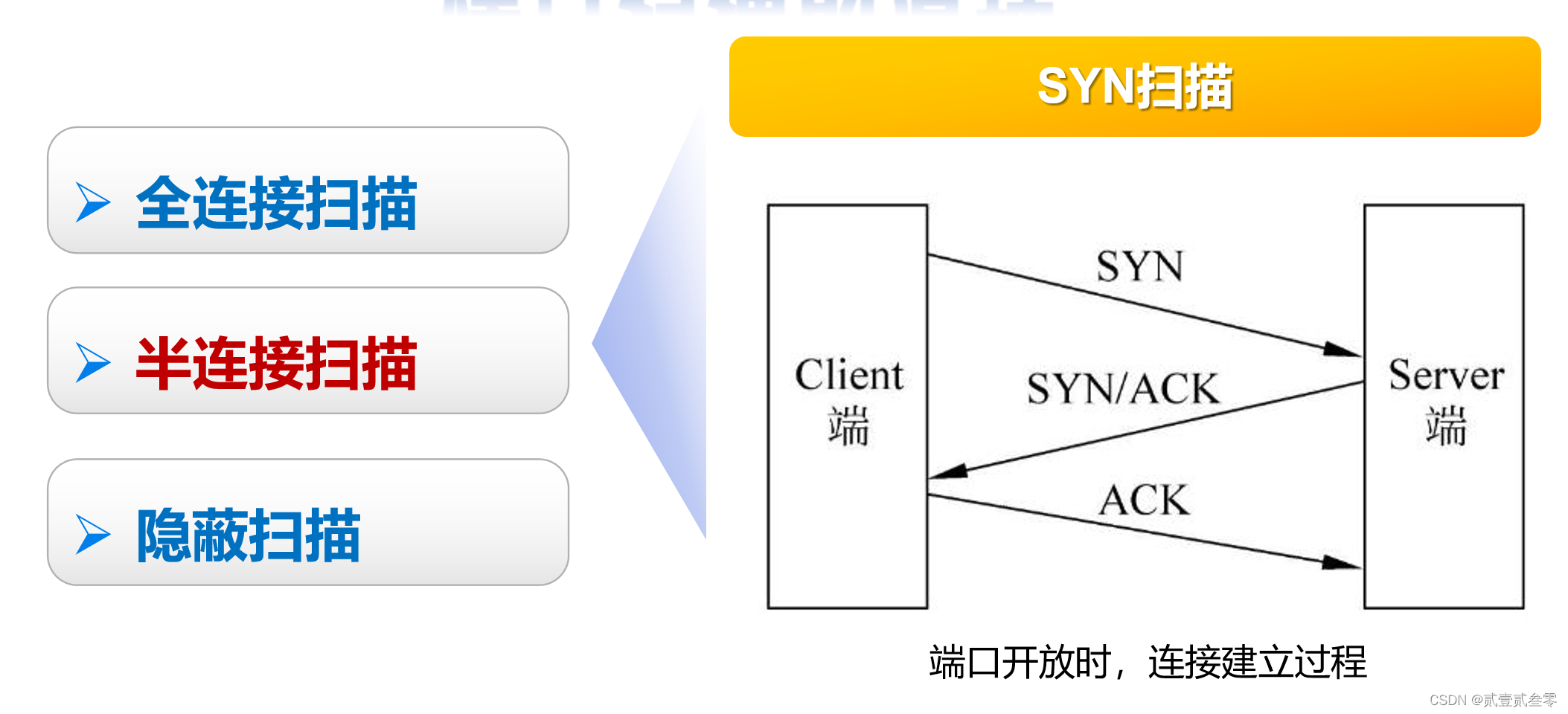
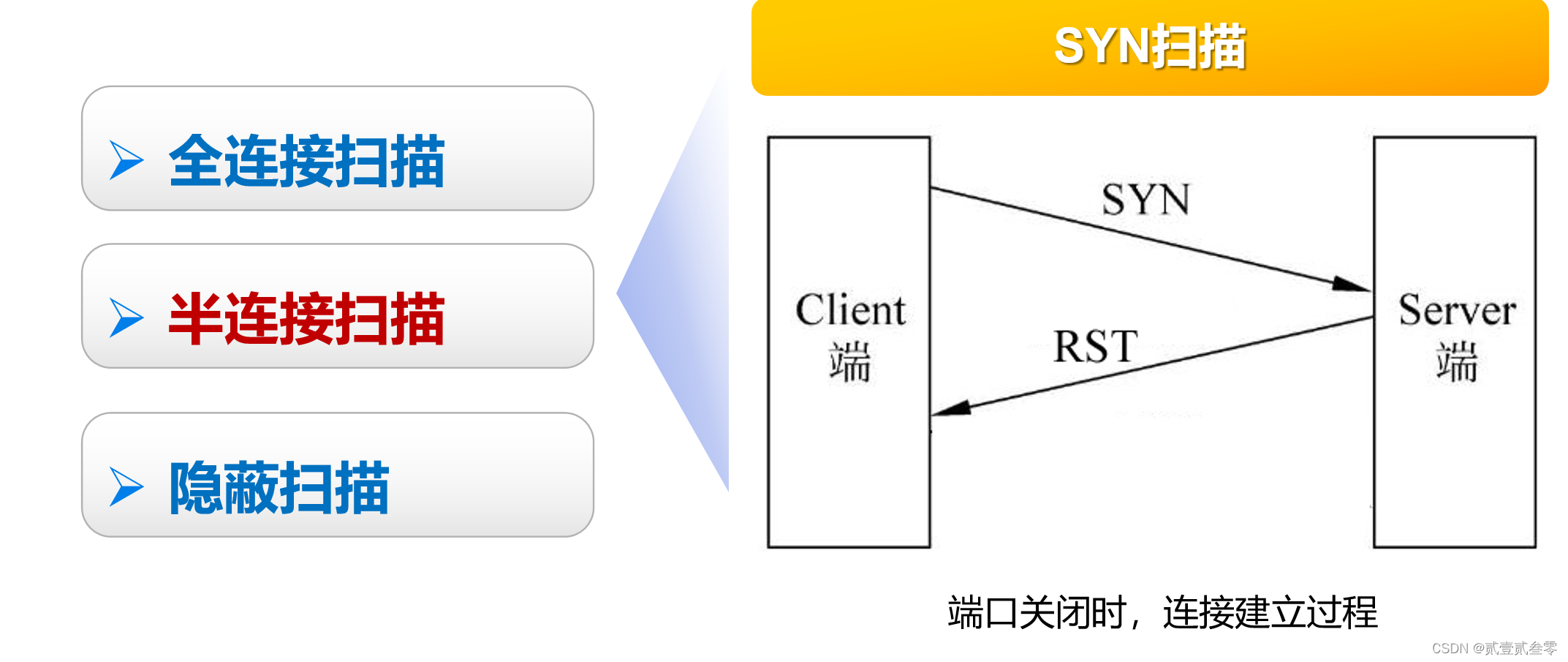
SYN扫描也称半开放扫描。在SYN扫描中,恶意客户企图跟服务器在每个可能的端口建立TCP/IP连接。这通过向服务器每个端口发送一个SYN数据包,装作发起一个三方握手来实现。如果服务器从特定端口返回SYN/ACK(同步应答)数据包,则意味着端口是开放的。然后,恶意客户程序发送一个RST数据包。结果,服务器以为存在一个通信错误,以为客户端决定不建立连接。开放的端口因而保持开放,易于受到攻击。如果服务器从特定端口返回一个RST数据包,这表示端口是关闭的,不能攻击。通过向服务器连续发送大量的SYN数据包,黑客能够消耗服务器的资源。由于服务器被恶意客户的请求所淹没,不能或者只能跟很少合法客户建立通信。
优点:未建立TCP连接,不会被记录到系统日志中,扫描隐蔽
缺点:需要攻击者拥有客户机的root权限,可以被防火墙检测和过滤
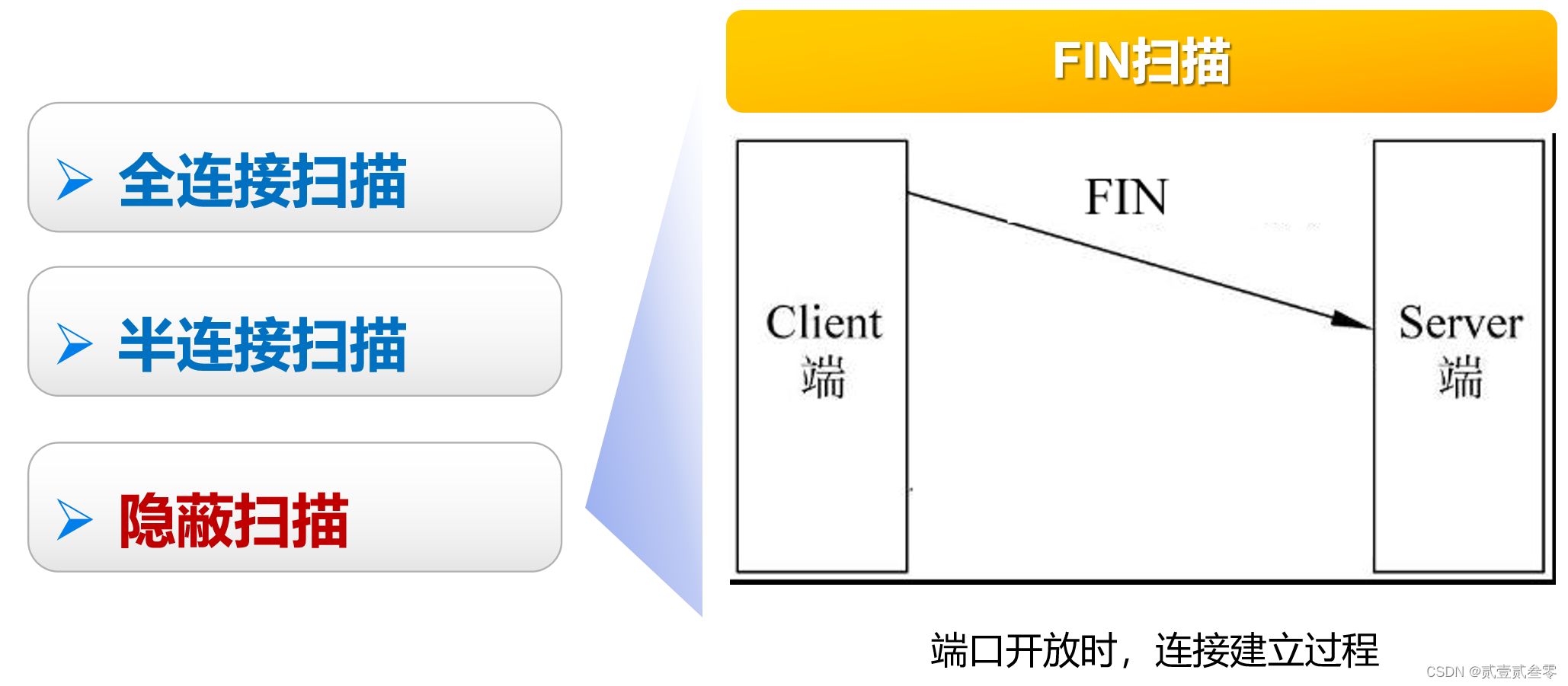
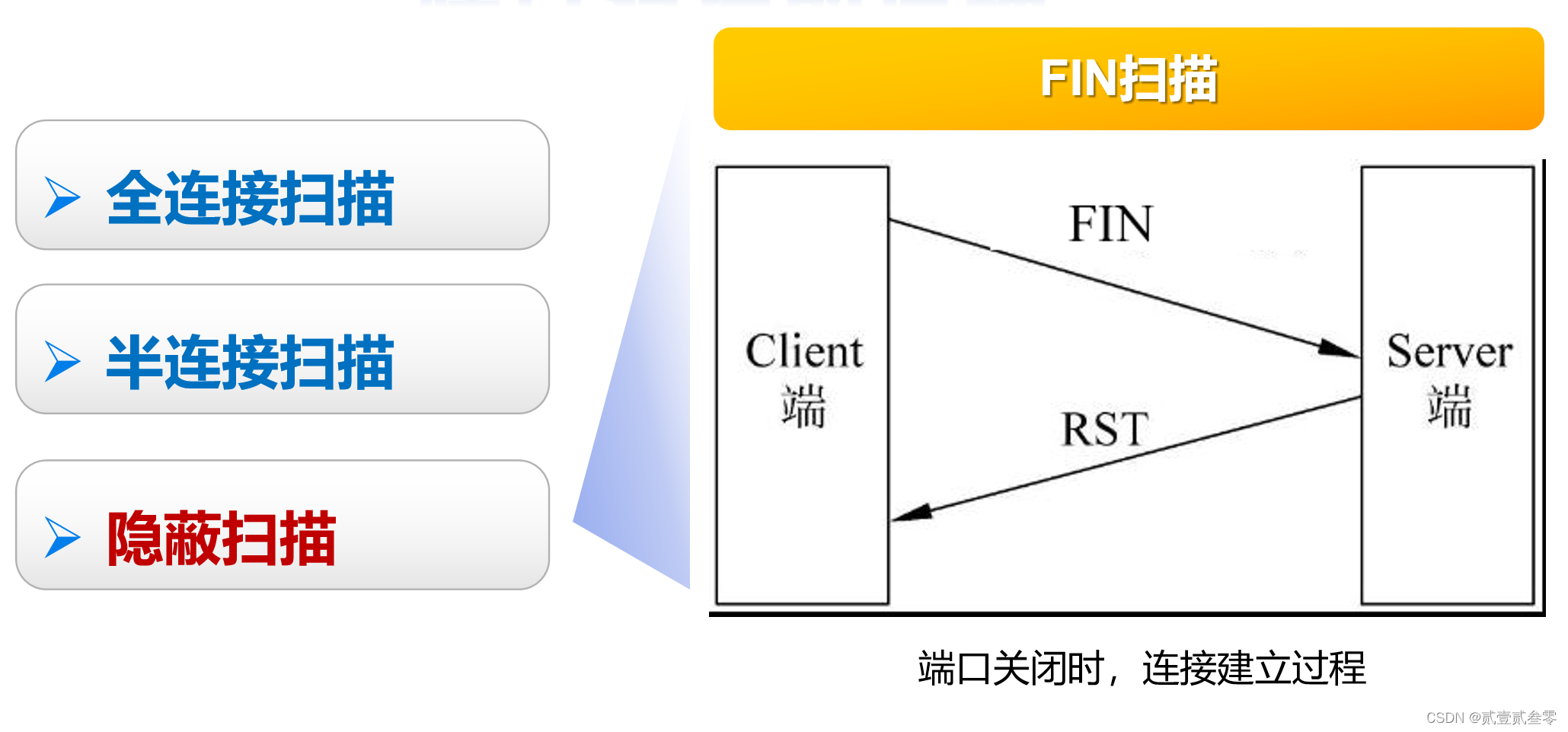
当我们发送一个FIN=1的报文到一个关闭的端口时,该报文会被目标主机丢弃,并随之返回一个RST报文;而对于一个开启的端口,该报文仍然会被丢弃,但不会有RST报文返回。可以由以上两点来辨别端口的状态;
优点:隐蔽性高,能穿透一般防火墙或者IDS系统,目标主机上也不会留下痕迹
缺点:数据包容易被丢弃,精确度偏低,只对Unix有效,对Windows无效(可以据此作为参考依据,来判断目的主机的操作系统)。
nmap
主机发现
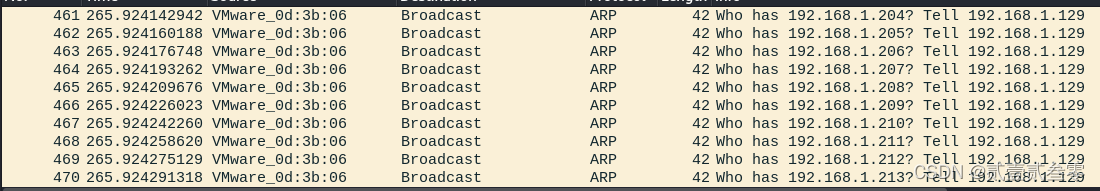
使用ARP协议进行主机发现
┌──(root㉿hnsw)-[~/桌面] └─# nmap -sn 192.168.1.0/24 Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-16 18:32 CST Nmap scan report for 192.168.1.1 Host is up (0.000063s latency). MAC Address: 00:50:56:C0:00:08 (VMware) Nmap scan report for 192.168.1.2 Host is up (0.000057s latency). MAC Address: 00:50:56:EC:C6:96 (VMware) Nmap scan report for 192.168.1.128 Host is up (0.00016s latency). MAC Address: 00:0C:29:4D:C3:71 (VMware) Nmap scan report for 192.168.1.254 Host is up (0.000088s latency). MAC Address: 00:50:56:EC:F0:8D (VMware) Nmap scan report for 192.168.1.129 Host is up. Nmap done: 256 IP addresses (5 hosts up) scanned in 6.08 seconds - 对单个主机的扫描
┌──(root㉿hnsw)-[~/桌面] └─# nmap 192.168.1.131 Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-16 19:42 CST Nmap scan report for 192.168.1.131 Host is up (0.0020s latency). Not shown: 977 closed tcp ports (reset) PORT STATE SERVICE 21/tcp open ftp 22/tcp open ssh 23/tcp open telnet 25/tcp open smtp 53/tcp open domain 80/tcp open http 111/tcp open rpcbind 139/tcp open netbios-ssn 445/tcp open microsoft-ds 512/tcp open exec 513/tcp open login 514/tcp open shell 1099/tcp open rmiregistry 1524/tcp open ingreslock 2049/tcp open nfs 2121/tcp open ccproxy-ftp 3306/tcp open mysql 5432/tcp open postgresql 5900/tcp open vnc 6000/tcp open X11 6667/tcp open irc 8009/tcp open ajp13 8180/tcp open unknown MAC Address: 00:0C:29:7D:1D:52 (VMware) Nmap done: 1 IP address (1 host up) scanned in 2.26 seconds 指定端口扫描
除了所有前面讨论的扫描方法, Nmap提供选项说明那些端口被扫描以及扫描是随机还是顺序进行。 默认情况下,Nmap用指定的协议对端口1到1024以及nmap-services 文件中列出的更高的端口在扫描。
-sT (TCP connect()扫描)
扫描开放端口
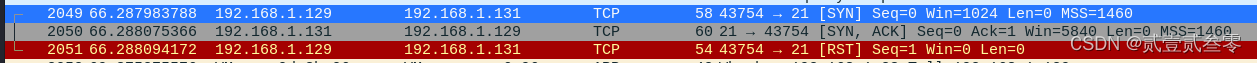
┌──(root㉿hnsw)-[~/桌面] └─# nmap -sT -p 21 192.168.1.131 Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-16 19:49 CST Nmap scan report for 192.168.1.131 Host is up (0.00011s latency). PORT STATE SERVICE 21/tcp open ftp MAC Address: 00:0C:29:7D:1D:52 (VMware) Nmap done: 1 IP address (1 host up) scanned in 2.11 seconds
一次完整的三次握手
-sS (TCP SYN扫描)
扫描开放端口
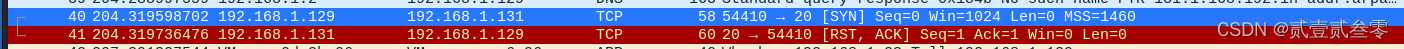
┌──(root㉿hnsw)-[~/桌面] └─# nmap -sS -p 21 192.168.1.131 Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-16 19:43 CST Nmap scan report for 192.168.1.131 Host is up (0.00016s latency). PORT STATE SERVICE 21/tcp open ftp MAC Address: 00:0C:29:7D:1D:52 (VMware) Nmap done: 1 IP address (1 host up) scanned in 2.17 seconds 扫描关闭端口
┌──(root㉿hnsw)-[~/桌面] └─# nmap -sS -p 20 192.168.1.131 Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-16 19:53 CST Nmap scan report for 192.168.1.131 Host is up (0.00011s latency). PORT STATE SERVICE 20/tcp closed ftp-data MAC Address: 00:0C:29:7D:1D:52 (VMware) Nmap done: 1 IP address (1 host up) scanned in 2.19 seconds -sF (FIN扫描)
┌──(root㉿hnsw)-[~/桌面] └─# nmap -sF -p 21 192.168.1.131 Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-16 19:55 CST Nmap scan report for 192.168.1.131 Host is up (0.00011s latency). PORT STATE SERVICE 21/tcp open|filtered ftp MAC Address: 00:0C:29:7D:1D:52 (VMware) Nmap done: 1 IP address (1 host up) scanned in 2.37 seconds ┌──(root㉿hnsw)-[~/桌面] └─# nmap -sF -p 20 192.168.1.131 Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-16 19:55 CST Nmap scan report for 192.168.1.131 Host is up (0.00013s latency). PORT STATE SERVICE 20/tcp closed ftp-data MAC Address: 00:0C:29:7D:1D:52 (VMware) Nmap done: 1 IP address (1 host up) scanned in 2.20 seconds 使用Nmap进行扫描目标操作系统
目标的操作系统类型是一个十分重要的信息,如果我们知道了目标所使用的操作系统之后就可以大大的减小工作量。例如我们知道了目标系统为Windows XP,那么就不必再进行一些针对Linux系统的渗透测试方法了。同样如果目标系统为Windows 10,那么之前的MS08—067这些针对Windows XP系统的渗透模块也就不需要测试了。通常,越老旧的系统也就意味着越容易被渗透,所以我们在进行渗透测试的时候往往希望能找到目标网络中那些比较老的系统。
Nmap最著名的功能之一是用TCP/IP协议栈fingerprinting进行远程操作系统探测。 Nmap发送一系列TCP和UDP报文到远程主机,检查响应中的每一个比特。 在进行一打测试如TCP ISN采样,TCP选项支持和排序,IPID采样,和初始窗口大小检查之后, Nmap把结果和数据库nmap-os-fingerprints中超过 1500个已知的操作系统的fingerprints进行比较,如果有匹配,就打印出操作系统的详细信息。 每个fingerprint包括一个自由格式的关于OS的描述文本, 和一个分类信息,它提供供应商名称(如Sun),下面的操作系统(如Solaris),OS版本(如10), 和设备类型(通用设备,路由器,switch,游戏控制台, 等)。
采用下列选项启用和控制操作系统检测:
┌──(root㉿hnsw)-[~/桌面] └─# nmap -O 192.168.1.131 Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-16 20:01 CST Nmap scan report for 192.168.1.131 Host is up (0.00051s latency). Not shown: 977 closed tcp ports (reset) PORT STATE SERVICE 21/tcp open ftp 22/tcp open ssh 23/tcp open telnet 25/tcp open smtp 53/tcp open domain 80/tcp open http 111/tcp open rpcbind 139/tcp open netbios-ssn 445/tcp open microsoft-ds 512/tcp open exec 513/tcp open login 514/tcp open shell 1099/tcp open rmiregistry 1524/tcp open ingreslock 2049/tcp open nfs 2121/tcp open ccproxy-ftp 3306/tcp open mysql 5432/tcp open postgresql 5900/tcp open vnc 6000/tcp open X11 6667/tcp open irc 8009/tcp open ajp13 8180/tcp open unknown MAC Address: 00:0C:29:7D:1D:52 (VMware) Device type: general purpose Running: Linux 2.6.X OS CPE: cpe:/o:linux:linux_kernel:2.6 OS details: Linux 2.6.9 - 2.6.33 Network Distance: 1 hop OS detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 3.57 seconds 相对操作系统而言,那些安装在操作系统之上的软件更是网络安全的重灾区。所以在对目标进行渗透测试的时候,要尽量的检测出目标系统运行的各种软件。
┌──(root㉿hnsw)-[~/桌面] └─# nmap -A 192.168.1.131 Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-16 20:02 CST Nmap scan report for 192.168.1.131 Host is up (0.00020s latency). Not shown: 977 closed tcp ports (reset) PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 2.3.4 | ftp-syst: | STAT: | FTP server status: | Connected to 192.168.1.129 | Logged in as ftp | TYPE: ASCII | No session bandwidth limit | Session timeout in seconds is 300 | Control connection is plain text | Data connections will be plain text | vsFTPd 2.3.4 - secure, fast, stable |_End of status |_ftp-anon: Anonymous FTP login allowed (FTP code 230) 22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0) | ssh-hostkey: | 1024 600fcfe1c05f6a74d69024fac4d56ccd (DSA) |_ 2048 f211ddea72bae61b1243de8f3 (RSA) 23/tcp open telnet Linux telnetd 25/tcp open smtp Postfix smtpd | sslv2: | SSLv2 supported | ciphers: | SSL2_RC4_128_WITH_MD5 | SSL2_RC4_128_EXPORT40_WITH_MD5 | SSL2_DES_192_EDE3_CBC_WITH_MD5 | SSL2_DES_64_CBC_WITH_MD5 | SSL2_RC2_128_CBC_EXPORT40_WITH_MD5 |_ SSL2_RC2_128_CBC_WITH_MD5 |_ssl-date: 2024-04-16T12:03:43+00:00; +5s from scanner time. | ssl-cert: Subject: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX | Not valid before: 2010-03-17T14:07:45 |_Not valid after: 2010-04-16T14:07:45 |_smtp-commands: metasploitable.localdomain, PIPELINING, SIZE , VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN 53/tcp open domain ISC BIND 9.4.2 | dns-nsid: |_ bind.version: 9.4.2 80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2) |_http-server-header: Apache/2.2.8 (Ubuntu) DAV/2 |_http-title: Metasploitable2 - Linux 111/tcp open rpcbind 2 (RPC #) | rpcinfo: | program version port/proto service | 2 111/tcp rpcbind | 2 111/udp rpcbind | 2,3,4 2049/tcp nfs | 2,3,4 2049/udp nfs | 1,2,3 50808/tcp mountd | 1,2,3 59107/udp mountd | 1,3,4 44878/udp nlockmgr | 1,3,4 54620/tcp nlockmgr | 1 41348/tcp status |_ 1 56209/udp status 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP) 512/tcp open exec netkit-rsh rexecd 513/tcp open login OpenBSD or Solaris rlogind 514/tcp open tcpwrapped 1099/tcp open java-rmi GNU Classpath grmiregistry 1524/tcp open bindshell Metasploitable root shell 2049/tcp open nfs 2-4 (RPC #) 2121/tcp open ftp ProFTPD 1.3.1 3306/tcp open mysql MySQL 5.0.51a-3ubuntu5 | mysql-info: | Protocol: 10 | Version: 5.0.51a-3ubuntu5 | Thread ID: 8 | Capabilities flags: 43564 | Some Capabilities: Support41Auth, SupportsTransactions, SupportsCompression, LongColumnFlag, SwitchToSSLAfterHandshake, Speaks41ProtocolNew, ConnectWithDatabase | Status: Autocommit |_ Salt: p5X<_MA?Y!710="0jF`/ 5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7 |_ssl-date: 2024-04-16T12:03:33+00:00; +5s from scanner time. | ssl-cert: Subject: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX | Not valid before: 2010-03-17T14:07:45 |_Not valid after: 2010-04-16T14:07:45 5900/tcp open vnc VNC (protocol 3.3) | vnc-info: | Protocol version: 3.3 | Security types: |_ VNC Authentication (2) 6000/tcp open X11 (access denied) 6667/tcp open irc UnrealIRCd | irc-info: | users: 1 | servers: 1 | lusers: 1 | lservers: 0 | server: irc.Metasploitable.LAN | version: Unreal3.2.8.1. irc.Metasploitable.LAN | uptime: 0 days, 0:23:13 | source ident: nmap | source host: F6A37901.78DED367.FFFA6D49.IP |_ error: Closing Link: gujnhpfgc[192.168.1.129] (Quit: gujnhpfgc) 8009/tcp open ajp13 Apache Jserv (Protocol v1.3) |_ajp-methods: Failed to get a valid response for the OPTION request 8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1 |_http-favicon: Apache Tomcat |_http-title: Apache Tomcat/5.5 |_http-server-header: Apache-Coyote/1.1 MAC Address: 00:0C:29:7D:1D:52 (VMware) Device type: general purpose Running: Linux 2.6.X OS CPE: cpe:/o:linux:linux_kernel:2.6 OS details: Linux 2.6.9 - 2.6.33 Network Distance: 1 hop Service Info: Hosts: metasploitable.localdomain, irc.Metasploitable.LAN; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_nbstat: NetBIOS name: METASPLOITABLE, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox) |_smb2-time: Protocol negotiation failed (SMB2) |_clock-skew: mean: 1h00m05s, deviation: 2h00m00s, median: 4s | smb-os-discovery: | OS: Unix (Samba 3.0.20-Debian) | Computer name: metasploitable | NetBIOS computer name: | Domain name: localdomain | FQDN: metasploitable.localdomain |_ System time: 2024-04-16T08:03:23-04:00 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) TRACEROUTE HOP RTT ADDRESS 1 0.20 ms 192.168.1.131 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 49.79 seconds 如果想节约扫描时间,也可以用-sV参数粗略扫描
┌──(root㉿hnsw)-[~/桌面] └─# nmap -sV 192.168.1.131 Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-16 20:05 CST Nmap scan report for 192.168.1.131 Host is up (0.0025s latency). Not shown: 977 closed tcp ports (reset) PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 2.3.4 22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0) 23/tcp open telnet Linux telnetd 25/tcp open smtp Postfix smtpd 53/tcp open domain ISC BIND 9.4.2 80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2) 111/tcp open rpcbind 2 (RPC #) 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 512/tcp open exec netkit-rsh rexecd 513/tcp open login OpenBSD or Solaris rlogind 514/tcp open tcpwrapped 1099/tcp open java-rmi GNU Classpath grmiregistry 1524/tcp open bindshell Metasploitable root shell 2049/tcp open nfs 2-4 (RPC #) 2121/tcp open ftp ProFTPD 1.3.1 3306/tcp open mysql MySQL 5.0.51a-3ubuntu5 5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7 5900/tcp open vnc VNC (protocol 3.3) 6000/tcp open X11 (access denied) 6667/tcp open irc UnrealIRCd 8009/tcp open ajp13 Apache Jserv (Protocol v1.3) 8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1 MAC Address: 00:0C:29:7D:1D:52 (VMware) Service Info: Hosts: metasploitable.localdomain, irc.Metasploitable.LAN; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 17.46 seconds 免责声明:本站所有文章内容,图片,视频等均是来源于用户投稿和互联网及文摘转载整编而成,不代表本站观点,不承担相关法律责任。其著作权各归其原作者或其出版社所有。如发现本站有涉嫌抄袭侵权/违法违规的内容,侵犯到您的权益,请在线联系站长,一经查实,本站将立刻删除。 本文来自网络,若有侵权,请联系删除,如若转载,请注明出处:https://haidsoft.com/132227.html